How to fix the “Deceptive site ahead” error: 4 steps to remove it
“Deceptive site ahead” is a warning message by Google Chrome for sites it views as unsafe. Its appearance implies that Google has blocklisted a malicious website due to certain security concerns.

The deceptive site warning is part of Chrome’s security measures to combat frequent cyber attacks. It hinders visitors from accessing potentially dangerous websites that may jeopardize visitors’ sensitive information, such as credit card details and login credentials.
Here’s a breakdown of the “Deceptive site ahead” warning message, including its variations and possible causes:
| Error code | Deceptive site ahead |
| Error type | Warning |
| Error variations | The site ahead contains malware The site ahead contains harmful programs Deceptive website warning Continue to [website name]? This page is trying to load scripts from unauthenticated sources |
| Error causes | Backlinks to questionable websites or malicious domains Malware infection Malicious files Phishing pages Deceptive content Compromised SSL certificates Virus infection Malicious backdoor code |
What Is the “Deceptive Site Ahead” Warning?
This warning refers specifically to sites likely to be phishing scams, where they imitate genuine websites to illicitly collect users’ personal details.
4 Steps to remove the “Deceptive site ahead” warning
Despite the warning’s indication of malware, sometimes Google flags websites by mistake.
Before submitting a review request to Google, check other browsers for the warning. If you’ve fixed security issues recently, clear the browser’s cache. It will force Chrome to reload the site’s latest version.
Should the “Deceptive site ahead” warning persist, follow the steps below to fix the issue. Keep in mind that this tutorial will focus on WordPress websites. That said, some methods may work on sites running on other platforms.
1. Detect the cause of the problem
To resolve the warning, you need to locate the source of the problem. First, use Google Safe Browsing to verify your site’s status. This free Google tool will detect any malware or phishing threats that made the web browser deem the website unsafe.

Google Search Console, previously known as Google Webmaster Tools, has a similar feature that detects security issues within websites. However, this method will only work if you have connected the site to Google Search Console and still have access to the platform.

Alternatively, deep scan your website using a malware scanner. This method is ideal for users with limited technical knowledge, as the tool will do all the work for you. Plenty of online malware scanners like SiteGuarding and Quttera offer this service for free.

Pro Tip
Hostinger also provides a convenient in-built malware scanner to protect your website.
If you’re familiar with coding and scripting languages, you may choose the manual route. Use the developer tools to inspect Chrome’s elements and check the site’s source code for suspicious third-party elements. Then, use Hostinger’s File Manager to compare your findings with the original files. This will help you find any compromised files.
When checking your website, note any new themes or plugins you installed. Hackers exploit themes and plugins with cross-site scripting (XSS) attacks forcing visitors to run malicious scripts in their browsers.
Also, check recent files, as they are likely infected. Connect to an SSH terminal and type the “ls” Linux command to list all directories’ files and their details, such as creation dates and permissions.
We recommend using PuTTY as your SSH client. This free software works on Windows, Linux, and macOS operating systems.

Here are some of the most common causes of the “Deceptive site ahead” error:
- Malware and virus infection
- URL injection
- Phishing pages
- Vulnerabilities in plugins and themes
- Suspicious backlinks
- Spam content
Important! If you, Google services, and the malware scanner cannot find any infected files within your website, Google might have blacklisted it by mistake. Report incorrect phishing warning to Google for warning removal ‒ we’ll provide more information on this process in the fourth step of this tutorial.
2. Back up your site
Before changing the infected website’s code, back up the files and databases. Doing so allows you to compare files and restore any lost data after the malware cleanup process.
There are several ways to back up a WordPress site. You can use a backup plugin, the web host’s solution, or back up manually via FTP and phpMyAdmin.
There are various backup plugins to help you automate your backup process. Here are our recommendations for the best freemium options:
- BackupWPup ‒ offers cloud-based storage, database check and repair, and scheduled backups.
- UpdraftPlus ‒ provides email reporting and multilingual support.
- Duplicator ‒ supports manual backups and file bundling.
Most web hosting providers offer an automatic site backup. Hostinger, for example, provides a one-click backup and restore feature accessible via hPanel.
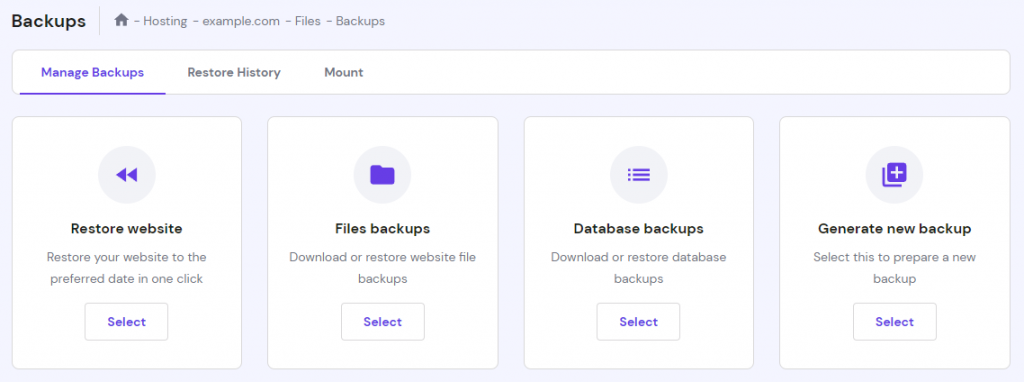
Alternatively, backup your site files manually using your web hosting’s file manager or the FileZilla FTP Client. phpMyAdmin should also be available via the hosting dashboard ‒ Hostinger users can access it to back up databases via hPanel.
Important! Keep the backup separated from the files that aren’t infected by malware.
3. Remove dangerous website files
Once you’ve identified the malicious code or infected website files, proceed to remove them.

WordPress users can install a security plugin to detect and remove malware from their sites. We recommend using Wordfence, a popular security plugin. It’s equipped with WordPress-optimized security features, such as a web application firewall and a server-side scanner.
Follow these steps to remove malware from a WordPress site using Wordfence:
- Install Wordfence Security from the WordPress repository and activate it.
- Navigate to Wordfence → Scan → Start New Scan from your WordPress dashboard.

- The list of the detected issues will be available in the Results Found section. Click on the Repair All Repairable Files button to fix the corrupted files.
Infected websites on other CMSs may use a malware removal tool instead. Most malware scanners let you remove infected files with a single click.
If you already have a backup from before your site was infected, restore it to replace the corrupted files. As some hosting providers keep backups for a limited time, contact your hosting provider for assistance if needed.
Important! Seek out a professional if you aren’t confident in your technical skills. Deleting the wrong files or code may further damage your WordPress website.
4. Request Google to review your site
Once your site is free from malware, the last step is to send a review request to Google so that the warning is removed.
Google Search Console provides a direct channel to submit your appeal. Navigate to Security & Manual Actions → Security Issues from the dashboard, then select Request a Review. The request should include information on your actions to resolve the issue.
Appeals for hacked websites generally need several weeks to process. Meanwhile, requests for phishing and malware issues take up to several days to review.
If Google approves your request, the search engine will lift your site from its blacklist and re-index the web pages. The “Deceptive site ahead” warning will disappear from your site within 72 hours.
Important! Make sure your site is completely free of any security issues before requesting a review. Having your request rejected numerous times will prompt Google into giving your site a Repeat Offender status for 30 days. You cannot request additional reviews during that period.
How does “Deceptive site ahead” impact your site?
As mentioned earlier, having the “Deceptive site ahead” warning on your site indicates that it may have been hacked. As the website owner, you risk of having all the site data stolen or deleted.
If malicious code causes extensive damage to your site, you’ll have to spend money to fix the problem. For instance, hiring a WordPress developer to recover the site will cost around $10-$66/hour. This excludes the time it will take to reach out to all involved parties regarding the security breach.
In the worst case, you may face legal consequences for not protecting your visitors’ personal information. This issue can ruin your brand’s reputation and lead to lost customer trust. With eCommerce sites, this will negatively impact the conversion and sales rates.
In terms of brand exposure, site traffic will also suffer as Google will actively hinder visitors from accessing the website. Even if you manage to take the hacked site back, you’ll still lose months or even years of hard work put into your WordPress SEO.
Prolonged malware infestation may also prompt your web host to remove the site and suspend your hosting account.
How to prevent the “Deceptive site ahead” warning?
While there are ways to fix the “Deceptive site ahead” warning error, it takes time and a lot of effort to resolve it. We recommend taking measures to minimize the risk of this issue happening in the first place.
Here’s how to debug WordPress and prevent the “Deceptive site ahead” warning error.
Invest in security plugins and software
Your WordPress website already has built-in security features. However, installing security plugins will further strengthen its defenses against malware attacks.
Numerous WordPress security plugins are available in the official directory and various marketplaces. This security software can equip you with firewalls and security scanners. These tools block malicious traffic and requests with infected content before they can damage your website.
There are free versions, but they usually offer limited features. Consider investing in premium plugins to get advanced security tools.

Here are our recommendations for the best WordPress security plugins besides Wordfence:
- Sucuri ($199.99-$499.99/year) ‒ offers malware and hack removal, advanced security scanning, and blocklist monitoring and removal services.
- Jetpack ($4.77-$47.97/month, billed annually) ‒ provides automated backups, malware scanners, and website optimization tools.
- All In One WP Security (free) ‒ comes with brute force login attack prevention, file change detection scanner, and front-end text copy protection features.

Your computer’s security is no less important. Antivirus and anti-malware software is a must-have tool for any active internet user as it prevents your local system from being infected.
The following are some of the best antivirus and anti-malware software available:
- Kaspersky ($29.99/year for three devices)
- Bitdefender Antivirus Plus ($29.99/year for three devices)
- Norton Antivirus Plus ($19.99/year per device)
- McAfee Antivirus ($34.99/year per device)
- ESET NOD32 Antivirus ($39.99/year per device)
Pick a secure hosting provider
Besides websites, hackers also target web servers by compromising hosting accounts. As part of their services, web hosting companies are responsible for securing all data hosted on their servers. For this reason, it’s important to pick a hosting provider with the best server security measures.
Non tech-savvy WordPress users should host their sites on managed WordPress servers. This type of hosting takes care of system security and automates updates, minimizing the possibility of human error.
All of Hostinger’s managed WordPress hosting plans come with a free SSL certificate and LiteSpeed’s cache engine. Besides providing 24/7 WordPress support, Hostinger also performs weekly website backups.

Use an SSL certificate
Security Sockets Layer (SSL) is an encryption-based protocol that secures connections between servers and browsers. A website that has an SSL certificate will transmit data using Hypertext Transfer Protocol Secure (HTTPS). This is indicated by https:// at the start of its URL and a padlock icon in the address bar.
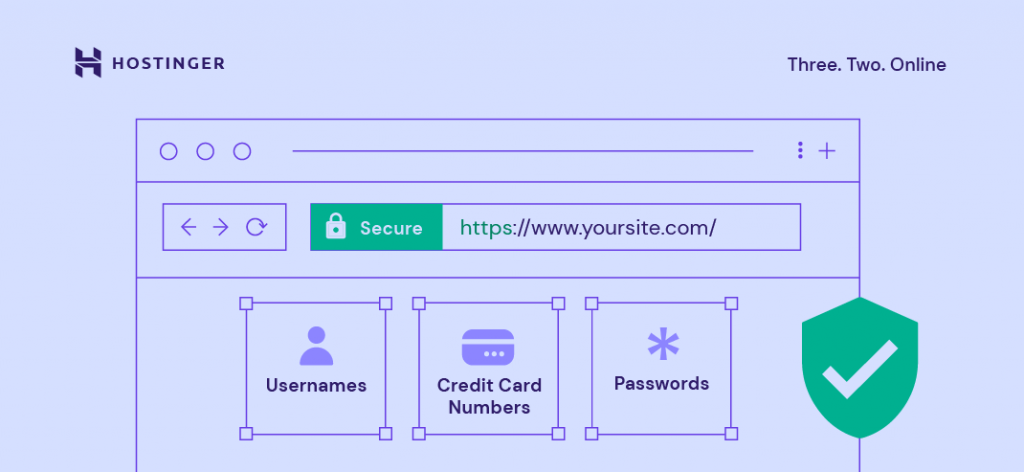
Google encourages websites to get an SSL certificate to promote internet safety. Besides making SSL one of the ranking factors, it also flags websites that haven’t moved to HTTPS with the deceptive site warning.
If your WordPress site doesn’t have an SSL certificate yet, we recommend getting one as soon as possible. Enabling it will improve your site’s branding and attract potential traffic, in addition to avoiding Google’s penalty.
Some hosting providers, like Hostinger, include a free SSL certificate with their hosting services. Alternatively, buy one from a Certified Authority that issues digital certificates for data encryption.
Once you have obtained an SSL certificate, don’t forget to redirect your website to HTTPS. Otherwise, visitors will still access it via HTTP protocol.
Do regular updates
Building your website on WordPress comes with better scalability and customization. However, you are responsible for maintaining it to ensure good performance and security.
Keeping the website’s system and supporting software updated is very important. This means updating WordPress core files, themes, and plugins to the latest version.
Besides improving the site’s performance, updates patch security vulnerabilities from the previous versions. Therefore, updating your website regularly will optimize its security against malware.
You can enable WordPress auto-updates to save time and minimize the chance of human error.
Important! Back up your website before doing major core release updates to avoid losing data in case the update fails.
Practice safe browsing
Downloading files or software from dangerous websites puts you at risk for malware, viruses, and identity theft. Hackers can disguise malware as executable files and run malicious software when you click on them.
Malware may get into your device through illegal downloads, fake security pop-ups, and phishing emails. Hackers also often lure users into accessing a fake site and giving out their personal information.
Therefore, you should always be vigilant when browsing the web, particularly when looking for a file or software to download.
The following are tips for practicing safe browsing:
- Download files from reputable, verified sites only.
- Pay attention to malware warnings.
- Avoid clicking on security pop-ups and ads about security vulnerabilities within your device.
- Scan files and software for malware and viruses before opening them.
- Be wary of .exe and .scr file extensions, especially if you’re downloading non-executable files.
Your device may have malware if it suddenly crashes, won’t shut down or restart, or doesn’t let you remove particular software. Suspicious toolbars and icons may appear on your desktop and browser. You may also see ads and pop-ups when opening legitimate sites.
If your device displays these behaviors, immediately run a deep scan with your antivirus or seek professional help.
Protect your site login
One of the best ways to improve your WordPress security is by securing the login page. Doing so will help prevent brute force attacks which use trial-and-error to crack login credentials.
As the site’s administrator, the least you can do is use secure login credentials. Create a strong username and password using a combination of numbers, upper- and lowercase letters, and special characters. Plenty of password generators can generate a strong password in one click.
Another way to reinforce your login page is to enable 2FA authentication. A unique code from a third-party app, like Google Authenticator, can unlock the extra security.
Some WordPress security plugins like Wordfence Login Security also let you enable 2FA authentication on your site.

To further strengthen your site security, add password protection for website directories. This security practice limits access to parts of your website.
Hostinger users can follow these steps to password-protect their site:
- Navigate to Advanced → Password Protect Directories from hPanel.
- Select the Directory textbox and pick which directory you want to protect. Add a chosen username and password to the respective textboxes.

- Click Protect. All the password-protected directories will appear on this page.
Manage user activity
A hacked WordPress site usually shows unusual user activities. They indicate that someone used a hacked or ghost account for unauthorized actions.
Keeping track of user activity logs and restricting users’ access will minimize this security risk. Knowing all the changes made to the site will also make fixing errors easier.
WordPress activity logs and tracking plugins like Simple History and WP Activity Log have the tools needed to make your job easier. We recommend choosing a plugin that has instant notification and reporting features.
Additionally, utilize WordPress user roles and permissions to limit users’ access within your site. If WordPress’s default roles don’t meet your needs, create new ones or edit the existing roles. You can manage user roles by navigating to Users → All Users from your WordPress dashboard.

Conclusion
The “Deceptive site ahead” message is a Google Safe Browsing warning error that appears on websites deemed unsafe for visitors. The causes of security breaches range from hacking attempts and malware infections to bad site security practices, such as invalid SSL certificates.
Here’s how to remove the “Deceptive site ahead” warning message:
- Find and pinpoint the cause of the problem.
- Back up your website.
- Remove dangerous website files.
- Request Google to review your site.
That said, it’s better to prevent the issue from occurring in the first place. Do so by investing in security plugins and reputable SSL certificate. Additionally, always practice safe browsing and regularly update your WordPress core files, plugins, and themes.
We hope this article helps you remove the “Deceptive site ahead” warning message from your website. Good luck!