How to set up passwordless SSH on Linux
Due to its reliability and security, the secure socket shell (SSH) is the most common way to interact with a remote server. However, using this protocol can be tedious since it uses a username and password by default.
To simplify the connection process, you can set up a passwordless SSH. Instead of the traditional username and password, this system uses an encrypted key pair to authenticate remote login.
In this article, we will explain how to set up passwordless SSH on Linux in four simple steps so you can connect to your server hassle-free.
Prerequisites
Before setting up passwordless SSH, make sure you can access your Linux virtual private server (VPS) using a username and password. This is important since we might need to add the authentication key manually.
Also, you must have superuser or root access to the VPS and your local machine. Since we will edit the system-level configuration, this will avoid permission errors.
If you can’t access your VPS via SSH as a superuser, check whether your hosting provider can help. For Hostinger users, you have full root access by default, meaning you can freely modify any aspect of your server.
Hostinger users can also connect to their server using the Browser terminal. This can be an alternative to passwordless SSH since you can interact with your VPS without entering credentials as long as you can access your hosting account.

Checking if SSH keys exist
If you are working with systems other than yours, such as a client’s computer, check whether it already has passwordless SSH set up.
Important! Setting up passwordless SSH on a local system that already has it will replace the existing authentication keys. This can cause connectivity issues that prevent you from accessing the previously paired server.
To check if your local system has passwordless SSH enabled, open Terminal and run this command:
ls -al ~/.ssh/id_*.pub
If you see the .pub file listed, which contains the authorization keys, the passwordless SSH is already active.

Otherwise, this output should show up:
ls: cannot access /users/appsadm/.ssh/id_*.pub: No such file or directory
Setting up passwordless SSH
After ensuring you meet all the prerequisites, follow these steps to set up passwordless SSH.
1. Generate SSH keys
To begin, let’s generate SSH keys – credentials that will replace the default username and password as the authentication token. Here’s how to do so:
- Open your local computer’s Terminal.
- Enter the following command to generate the SSH keys. You can use either rsa or ed25519 encryption:
ssh-keygen -t ed25519
- Hit Enter to save the SSH keys in the default location, which is ~/.ssh/. Alternatively, you can specify another location and hit Enter to confirm.
- Optionally, add a passphrase to encrypt your SSH keys. Hit Enter if you want to skip it.
Your command-line application should print the SSH keys’ randomart image and token. The SSH keys are automatically saved in the path you specified during the generation process earlier into two files – id_ed25519 and id_25519.pub.
Pro Tip
If you use Windows, you can generate the keys using an SSH client like PuTTY.
2. Copy the public key to the server
Now that you have obtained the SSH keys, copy the public one to your server.
Method 1: Using the ssh-copy-id command
The first method is the easiest and quickest one. To do so, simply enter the following command on your local machine’s Terminal:
ssh-copy-id remote_username@remote_IP_Address
Replace the remote_username with the user account on which you wish to enable passwordless SSH. Also, change remote_IP_Address to your VPS’s actual IP address.
Then, enter the user password. Once the setup is complete, your server will close the remote connection.
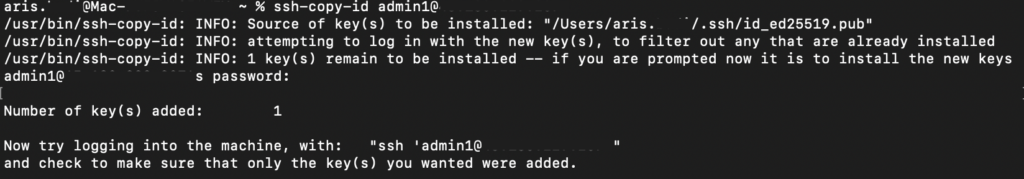
Note that passwordless SSH will only be active for the user you specify in the ssh-copy-id command. For example, you run the following command:
ssh-copy-id admin123@123.123.123.123
This means the passwordless SSH will only work for admin123, but not other users. Similarly, you won’t be able to log in from another client machine since it doesn’t have the key pair.
Important! To enable passwordless SSH for multiple devices or users, you must generate new keys for each of them.
Method 2: Copying the private key using SSH
You can copy your private key via SSH using a string of commands. Remember to replace the remote_username and remote_ip_address with their actual values:
cat ~/.ssh/id_ed25519.pub | ssh remote_username@remote_ip_address "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"
Your command-line interface should ask for the user’s password to initiate the connection.
This command fetches the content of your id_ed25519.pub file, connects to the server via SSH using the specified user, and adds the public key to the remote system’s authorized_keys folder.
Method 3: Manually copying the private key
If you can’t copy the private key using the remote command, add the credential manually. To do so, follow these steps:
- Open your local system’s command-line application and run this command. Replace ~/.ssh/id_25519.pub with the correct path if you are using a non-default location:
cat ~/.ssh/id_25519.pub
- Your command-line shell will output the public key. Copy and save it in a safe location.
- Connect to your remote machine via SSH using the below command. You can also connect via SSH using PuTTY:
ssh remote_username@remote_ip_address
- Once connected, create the .ssh directory using this command:
mkdir -p ~/.ssh
- Open your remote system’s .ssl/authorized_keys file using this command:
nano ~/.ssh/authorized_keys
- Paste the SSH key you copied earlier.
- Hit Ctrl + X, Y, and Enter to save the changes.
- Set the correct permissions to make sure your system can read the SSH public key while preventing unauthorized users from opening it.
chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keys
3. Verify key-based authentication
Let’s check whether the SSH passwordless login works properly. To do so, simply run the following in your local system’s command-line application:
ssh username@ip_address
You should automatically log in to the server as the specified user. If your command line asks for the password, check if you use the right account. Should the issue persist, try copying the SSH keys again.
If you enable a passphrase during the key generation process, you must enter it every time you log in. You can skip this process by caching the credential using an SSH agent. Here’s how to do so:
- Open your local system’s command-line application.
- Run the following command to start the SSH agent:
eval `ssh-agent -s`
- Cache your SSH key using this command. Remember to use the correct path if you change the default location :
ssh-add ~/.ssh/id_ed25519
Now, when accessing your server via SSH, your command-line application shouldn’t ask for a passphrase anymore.
4. Disable password-based SSH login
Although optional, it is advisable to disable password-based SSH login after setting up the authentication keys. This minimizes potential points of entry for cybercriminals, improving your VPS security.
Note that after disabling password-based login, you can only access your VPS using the computer on which you set up the SSH keys. To avoid getting locked out of your account, consider the following:
- Make sure your passwordless SSH works properly.
- Store your private key file, which resides on your local machine by default, in multiple locations. We highly recommend using a cloud-based, encrypted platform like 1Password or NordPass.
- Set up SSH keys on all systems that you will use to access your VPS. However, make sure these machines are secure.
Follow these steps to disable your password-based SSH login on your VPS:
- Log in to your server as root or a superuser. If you have done so, skip this step.
- Open the SSH configuration file using a text editor like Nano:
sudo nano /etc/ssh/sshd_config
- Find these settings and change the value according to the following example. If they start with a hash (#) sign, remove it to make sure the settings are active.
PasswordAuthentication no ChallengeResponseAuthentication no PubkeyAuthentication yes PermitRootLogin prohibit-password
- Press Ctrl + X, Y, and Enter to save the changes.
- Restart the SSH service using this command.
sudo systemctl restart sshd
Now, you can only log in to your server using the SSH keys.
Conclusion
Configuring passwordless SSH enables you to connect to your remote server more securely and easily. In this tutorial, we have explained how to set it up on a Linux server. Here are the steps:
- Open your local system’s Terminal or PuTTY and generate the SSH key pair.
- Copy the public key to your remote server using commands or manually via SSH.
- Verify the key-based login by connecting to your server.
- Disable your server’s password-based login by editing the SSHD file.
Repeat the steps if you wish to set up the passwordless login for another user or machine. Also, store your private SSH key in a safe, encrypted platform like 1Password to prevent you from getting locked out of your server.
Passwordless SSH FAQ
What is the best key type for passwordless SSH?
Two types of SSH keys – RSA and ED25519 – have their own pros and cons. RSA is compatible with more operating systems, especially older ones. Meanwhile, ED25519 is more secure and efficient because it is shorter.
Can I set up passwordless SSH for multiple servers?
Yes, you can set up passwordless SSH for multiple servers. Simply generate the authentication keys for each remote system and upload the public key to them. You can also set passwordless SSH for multiple local machines to access the same server.
Is it safe to disable password authentication entirely?
Yes, disabling password authentication on your VPS is generally safe since SSH keys are more difficult to crack, making them more secure. However, remember to safeguard your SSH keys and store them on a platform like 1Password to avoid getting locked out of your server.

Comments
March 22 2022
This blatantly doesn't work. I don't know what's wrong here, but that didn't work. It asked for a password anyway.
March 29 2022
Hey! Where did you get stuck? Did you manage to generate the SSH key?
April 25 2022
i noticed something similar, try with ssh -v and you can get a breakdown of whats working or not, some keys when you create them you can make an optional password with and i used another device to check my setup with similar scheme and it failed to connect because it was using a private key rather than public key to authenticate.